
Malware is a major threat to the security of computers, tablets, smartphones and all digital devices. Today’s cyberattacks frequently involves some type of malware. These malicious software can take many forms, from ransomware causing high damage and financial loss to simple boring adware, depending on the attackers’ objective.

Understanding these various types of malwares, their detection signals, and effective protection strategies has become essential for both individuals and organizations seeking to safeguard their digital data.
What is Malware?
Malware is defined as computer code specifically created to harm digital systems, networks, and users. This malicious software enters devices without authorization to extract sensitive data, damage systems, or disrupt operations. Cybercriminals develop these programs to compromise digital security for various gains.
The National Institute of Standards and Technology defines malware as software designed with harmful intent against data, computers, or networks. Unlike legitimate applications, malware arrives through deception, hiding its true function until activated.
Virus or Malware? Spot the difference!
The terms “virus” and “malware” are often used interchangeably, though they represent different concepts.
Computer viruses constitute a specific subset of malware characterized by self-replication and attachment to legitimate files or programs. Much like biological viruses require host cells, computer viruses need host programs to spread. Malware, in contrast, serves as the broader category covering all forms of malicious software, including viruses, worms, trojans, and ransomware.
This distinction emerged as threats diversified beyond the early virus-dominated era. By the mid-2000s, IT professionals had widely adopted “malware” as the standard terminology to reflect the growing variety of digital threats that didn’t rely on traditional viral spreading mechanisms.
Why Do Cybercriminals Use Malware?
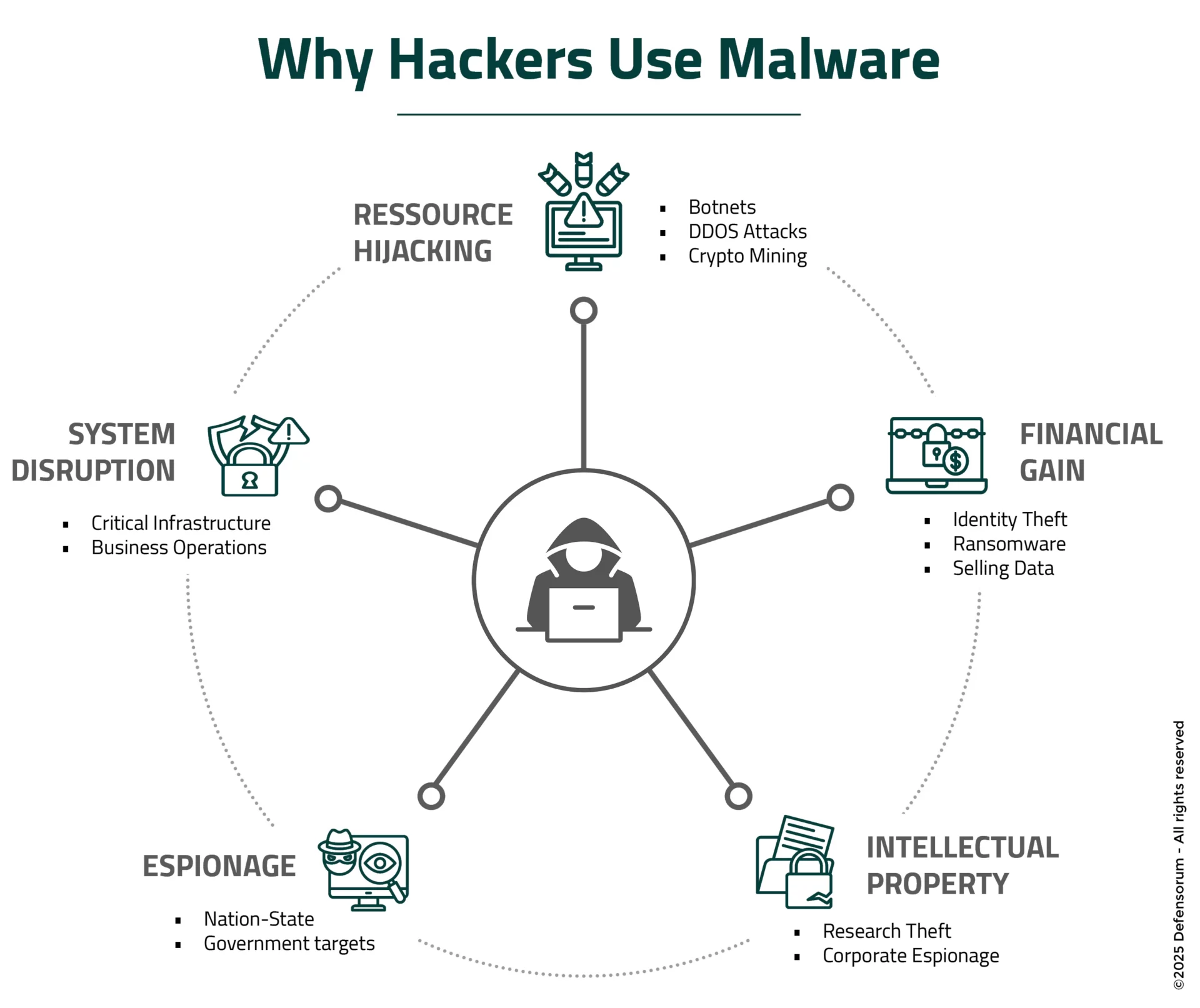
Cybercriminals deploy malware for numerous strategic purposes, with financial motivation ranking as the primary driver.

Attackers target personal credentials such as usernames, passwords, banking information, and Social Security numbers to facilitate identity theft and fraud.

Ransomware attacks represent a direct approach to monetary gain, with criminals encrypting vital data and demanding payment for restoration. Many attackers profit by gathering and selling sensitive information on dark web marketplaces, where personal data commands significant prices.

Beyond financial targets, malware serves as a tool for intellectual property theft, particularly against research institutions and corporations with valuable proprietary information. Nation-state actors and corporate spies use sophisticated malware to conduct espionage operations against governments and businesses.

System disruption constitutes another common objective, with attackers seeking to disable critical infrastructure or business operations. Malware can commandeer computing resources to form botnets—networks of compromised machines used for distributed denial-of-service attacks, spam distribution, or cryptocurrency mining without owner consent.

The tactics employed to achieve these goals include data exfiltration techniques, credential harvesting, system lockouts, network resource destruction, and botnet command operations. These methods often work in combination, with initial infections establishing footholds for additional malicious activities.
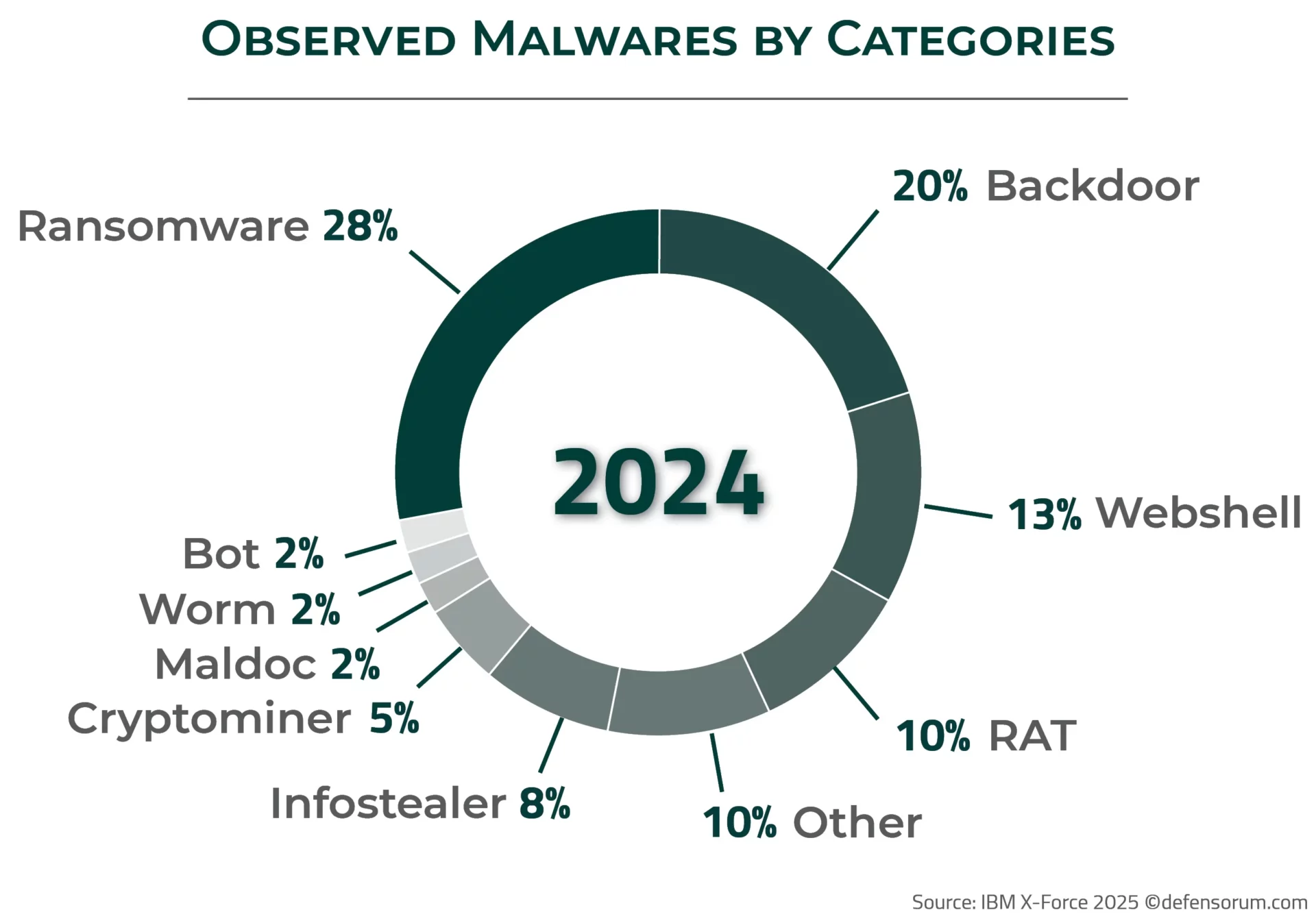
What Are the Main Types of Malware?
Malware can take many forms, each designed with specific attack methods and objectives.
In 2024, The distribution of malware types was as follows:
Ransomware
Ransomware is malicious software that blocks access to a computer or its files by encrypting them and demanding that the victim pay a ransom to regain access.

In many cases, cybercriminals exploit known vulnerabilities in software whose patches have not been updated, but ransomware can infiltrate in different ways:
- after opening a fraudulent attachment or malicious link received by e-mail ;
- when browsing compromised sites;
- following a computer intrusion on the victim’s system.
Ransomware encrypts valuable files and demands payment for decryption keys, effectively holding data hostage. Modern variants often implement “double extortion” tactics, threatening to publish stolen information if ransom demands remain unpaid.

Ransomware example: The ELENOR-Corp group uses Mimic ransomware to target healthcare organizations, encrypting data and demanding ransom.
ELENOR-Corp ransomware group attacks the healthcare sector
Backdoor
A backdoor is a malicious program used to give hackers unauthorized remote access to an infected computer by exploiting system vulnerabilities.

Backdoors establish concealed entry points into compromised systems, allowing attackers to bypass normal authentication and maintain persistent access regardless of password changes or security updates. These stealthy components often install following initial compromise through other malware types, creating long-term access for future exploitation.

Backdoor example: PondRAT malware disguised as legitimate Python packages was used to install backdoors in developer systems for remote access.
PondRAT backdoor hidden in Python packages hits developers
Web Shell
A web shell is a malicious script or program implemented by attackers on a web server to enable remote access and control. It functions as a backdoor, enabling unauthorized persons to execute commands, download and upload files, and manipulate the server.

These lightweight but powerful tools maintain a minimal footprint while enabling extensive server manipulation through a web browser interface.

Web shell example: Threat actors exploited Citrix NetScaler flaws to implant web shells and maintain hidden system access.
Vulnerabilities found in 1,900 Citrix NetScaler devices
Remote Access Trojan (RAT)
Remote Access Trojans (RAT) are malware designed to allow an attacker to remotely control an infected computer, including the mouse and keyboard, access to files and network resources.
RAT can infect computers via e-mail, be hosted on a malicious website or exploit a vulnerability in an unpatched machine.

Instead of destroying files or stealing data, a Trojan gives attackers complete control of a computer or mobile device, so they can silently browse applications and files, and bypass common security measures such as firewalls, intrusion detection systems and authentication controls.

RAT example : A memory-resident RAT built with PowerShell, spreading via a malicious Microsoft Word document sent as an email attachment, which communicates via DNS TXT records, making it difficult to detect.
New Powershell Remote Access Trojan Identified
Infostealer
An infostealer is a type of malware designed to penetrate computer systems and steal sensitive information. This may include login information (logs: passwords, e-mail addresses, browser history…), financial information or other personal data.

Often sold as Malware-as-a-Service (MaaS), the infostealer is a discreet tool that often goes undetected. Its strength lies in its ability to infiltrate computer systems without the owners being aware of its presence. The hacker’s aim is not to spy on the user in real time, but rather to retrieve all the interesting information present on the device, exfiltrate it and then disappear without a trace.
Infostealers are often used to gain access points and infiltrate networks. This enables attackers to gain access to computer systems for further attacks, such as ransomware. Recovered connection data can also be resold on darkweb marketplaces.
Cryptominer / Cryptojacking
Cryptojacking is a type of cyberattack in which a cybercriminal hijacks a computer or mobile device with a cryptominer to use its processing power to mine cryptocurrencies.

Unlike other types of malware, cryptominers don’t damage victims’ computers or data, but they do steal computer processing resources. This malware runs silently in the background, causing system slowdowns, increased power consumption and premature hardware deterioration due to intensive processing.
Cryptominer is usually installed on computers via a malicious link sent by email, through infected websites or online ads using self-executing JavaScript code to load mining code.

Cryptominer example: A large-scale campaign based on the Dofoil Trojan deployed a cryptominer on over 500,000 PCs in just 12 hours to extract Electroneum while avoiding detection.
500k PCs Infected with Cryptominer in 12 Hours by Dofoil Trojan
Maldoc
Maldocs (malicious documents) appear as legitimate files, but contain hidden malicious code designed to compromise systems when opened. These weaponized files circulate via compromised websites, e-mail attachments or file-sharing networks. They generally take the form of common working formats such as Word documents, PDFs, Excel spreadsheets or PowerPoint presentations…

What makes maldocs particularly effective is their familiar appearance, combined with the exploitation of trusted software. When opened, these documents execute embedded scripts to trigger the installation of malware.
While some maldocs require user interaction, such as the activation of macros, others exploit zero-day vulnerabilities requiring no additional authorization. The resulting infection can establish communication channels with the attacker’s infrastructure, download additional payloads or create persistence backdoors for long-term access.

Maldoc example: A malicious Word document with Python-based macros targeted MacOS systems to download encrypted malware payloads.
Malicious Word Macros Responsible for Spreading MacOS Malware
Worms
Worm is a type of malware capable of spreading or reproducing itself automatically without human interaction, enabling it to spread to other computers on a network. Unlike traditional malware that requires user’s action, worms infiltrate autonomously, using vulnerabilities to exploit systems.
Computer worms are defined by this ability to spread without user intervention. Once they have gained access to a computer, they can perform malicious actions.

Worms most often spread by exploiting unpatched vulnerabilities in software and operating systems or unsecured access protocols, through network drives and other access shared between several computers, or via removable media (USB sticks and external hard drives).
Worms are classified according to the way they spread from one machine to another. The most common are :
- E-mail worms: spread by sending e-mails containing malicious attachments.
- P2P worms: use peer-to-peer (P2P) networks to copy themselves onto other network users.
- Network worms: spread over the network using shared resources such as network drives.
- Instant messaging worms: spread via instant messaging such as Skype, WhatsApp, or Facebook Messenger by accessing an infected user’s contacts.
- Internet worms: infect websites and the computers that visit them by exploiting web browser vulnerabilities.

Worm example: Emotet, a network worm, infected a school district's systems, leading to significant financial loss due to its rapid propagation and data theft capabilities.
Rockingham School District loses $314,000 to Emotet malware
Malicious Bot
By definition, a bot is automated software that performs predefined tasks, usually on a network. A malicious bot is automated malware whose purpose is to infect a system, steal data or commit other fraudulent activities.

Malicious bots can be coordinated to conduct distributed denial-of-service attacks (DDoS), break into user accounts, send spam, distribute additional malware, or perform other malicious activities at scale.
A botnet refers to a network of computers infected by a malware bot, remotely controlled by a single hacker to carry out several coordinated actions simultaneously. The scale of a botnet (often made up of thousands to millions of bots) enables it to carry out large-scale attacks that would be impossible with simple malware.

Bot example: The dismantling of a botnet compromising SOHO routers has put an end to a stealth network used for espionage and access to US critical infrastructure systems.
FBI Targets Chinese KV Botnet in Cybersecurity Crackdown
Other Common Types of Malware
Keyloggers
A keylogger or keystroke logger is malware that infects a device to record the user’s keystrokes. Often placed on a computer when an infected application is downloaded, it enables the hacker to collect the credentials and other important information of a targeted user via a command and control (C&C) server. If programmed to do so, it can also spread to other devices in contact with an infected computer.
Rootkits
A rootkit is malware designed to enable hackers to access and control a target device in order to steal personal data and financial information, install malware or use computers as part of a botnet. It needs an infection vector to spread and install itself, often using Trojans or exploiting operating system vulnerabilities. Although most rootkits affect software and the operating system, some can also infect your computer’s hardware and firmware. Rootkits are able to conceal their presence, but although they remain hidden, they are always active.
Exploits
A computer exploit is malware that takes advantage of a security vulnerability in a software program, application or computer OS to gain illicit access to a system. These vulnerabilities are hidden in the code of the operating system and its applications, and exploits can be classified into several types, each with its own characteristics and methods of operation. The most common types are zero-day exploits, denial-of-service exploits and direct-access exploits. This type of attack often begins with spam and drive-by downloads. It encourages victims to open an infected attachment or click on links that redirect to a malicious website containing exploit code designed to take advantage of application weaknesses.
Spyware
Spyware is malware that infects a device to collect data and send it to hackers. It infects a device through conventional methods (attachments, malicious links, fraudulent sites, etc.) to gain access to personal information such as login credentials, financial details, or personal data, while operating invisibly in the background. This sensitive information is then resold to data companies, advertisers and other third-party users. Some variants provide remote access capabilities, allowing attackers to control the compromised device.
Adware
Short for “advertising supported software”, adware is malware that secretly installs itself on a computer to display unwanted ads and pop-ups on the screen. Often embedded within a free download or free application, adware can collect data and track user’s online behavior to display personalized content. While not primarily defined by their dangerous nature, adware slows down browsers and device operation, is unpleasant for users and can serve as a gateway for cybercriminals.
Fileless Malware
Fileless malware is malicious code that runs directly in a computer’s memory (i.e. RAM) rather than on the hard disk of a computer. Unlike conventional malware, no code is installed on the target system by the cyber attacker, making detection more difficult. Upon system reboot, this malware typically disappears from memory, complicating forensic analysis. This technique, which uses native tools to carry out a malicious attack, is known as “living off the land” (LOTL).
How does malware infect a device?
A malware attack relies on two factors: the malicious code itself and the attack vector, which is the mechanism used to deliver the malware to the intended target. Without an attack vector, the infection cannot spread, and malware remains harmless.
According to IBM X Force, the top initial access vectors for cyberthreats in 2024 were as follows:
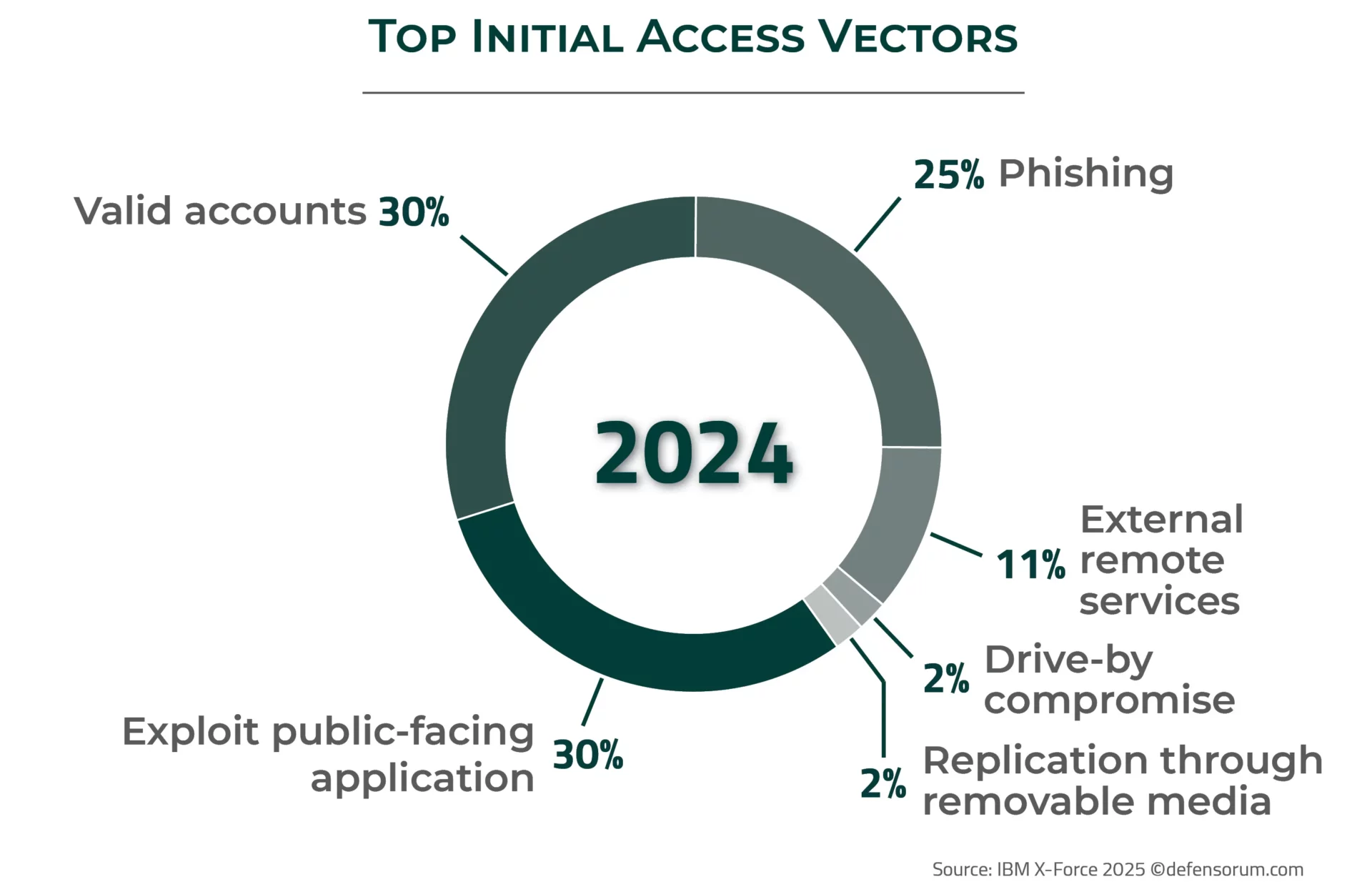
In detail, the most common known vectors of malware infection are as follows:
Exploit public-facing application
Public-facing applications can be exploited by attackers through a weakness in a host or system connected to the Internet to gain initial access to a network, targeting vulnerabilities in web servers, databases, or other services accessible on the Internet. This technique serves as a primary initial access method to breach organizational networks through externally exposed applications.

Web applications are valuable targets for malware distribution due to their accessibility and potential reach. Hackers systematically scan Internet-facing services, such as web servers, email systems, and remote access portals, looking for known vulnerabilities or configuration weaknesses. Once identified, these flaws become entry points for injecting malicious code directly into the application environment.
Common targets include content management systems, customer portals, and cloud-based applications that process user data. Organizations often struggle to provide the visibility and rapid patching required for these externally accessible systems, making them persistent vectors for malware infiltration.
Valid Accounts Compromise
Threat actors frequently exploit legitimate user credentials to distribute malware across organizational networks. Attackers can obtain and misuse existing account credentials to gain initial access to systems, where they can then deploy malware. These credentials can be acquired through various methods, including password spraying attacks, credential stuffing campaigns using previously hacked password databases, or social engineering techniques that trick users into divulging their login information.

This approach is particularly effective for distributing malware, as legitimate use of an account rarely triggers security alerts, allowing attackers to spread malicious code across networks while maintaining the appearance of normal user activity. This technique becomes even more dangerous when compromised accounts have administrative privileges, allowing attackers to disable security software and deploy malware to multiple systems simultaneously.
Social Engineering Tactics
Social Engineering is a manipulative technique that exploits human error to persuade individuals to perform actions that compromise their security, such as downloading malware. Psychological manipulation remains one of the most effective methods for distributing malware.
Phishing campaigns, which use deceptive emails or text messages to mislead recipients, represent the most widespread form of social engineering even though the attacks success rate has dropped from 46% in 2022 to 25% in 2024 (according to IBM X-Force). Despite the integration of AI technologies into phishing campaigns, this method seems less effective than exploiting vulnerabilities or credential-based attacks but still remains the 3rd most common initial access vector in 2024.

These deceptive communications often impersonate trusted organizations or individuals. Attackers devise messages designed to trigger emotional reactions – fear (“Security threats have been detected on your device”), financial incentive (“A payment in progress requires immediate action”) or time pressure (“Limited-time offer expires soon”) – in order to induce immediate action. The typical objective is to convince targets to open infected attachments or visit compromised websites that automatically install malware.
External Remote Service Compromise
Hackers are increasingly targeting remote access services (up in 2024) such as VPNs, Remote Desktop Protocol (RDP), and cloud-based virtual desktop infrastructures in order to gain access to corporate networks. These services, designed to provide legitimate remote connectivity to employees, create direct pathways into internal systems that bypass traditional perimeter defenses. Once inside through these channels, hackers can deploy malware across the entire corporate network.
Access can be gained through various methods, including brute-force attacks against weak passwords, exploiting unpatched vulnerabilities in VPN devices, or using compromised credentials. Organizations with poorly configured remote access solutions or lacking multi-factor authentication are particularly vulnerable to malware infiltration through these entry points.

Compromised VPN example: During the 2021 ransomware attack against Colonial Pipeline, hackers initially accessed network via a compromised VPN account in order to deploy on critical infrastructure systems.
How One Compromised VPN Account Brought Down Colonial Pipeline
Removable Media Exploitation
Cybercriminals can use USB drives, external hard drives, and mobile devices as initial vectors for spreading malware, particularly targeting isolated networks that are not connected to the internet.
« USB baiting » is a technique that involves placing infected USB storage devices in public places such as shared workspaces, libraries or any open space where targets are likely to find them. These devices often bear enticing labels or branding to increase their appeal to potential victims. Once inserted, the malware either runs automatically via the operating system’s autorun features or masquerades as legitimate application files to trick users into running them manually.
Mobile devices provide an additional avenue of infection when connected to corporate systems via USB cables. Smartphones and tablets can host malware that activates when mounted as external storage devices, with the connected system treating the mobile device in the same way as a traditional USB flash drive.
Malicious charging cables are a new variant of these attacks, in which seemingly harmless power cables contain embedded electronics capable of transmitting malicious payloads during normal device charging.
Software and System Vulnerabilities
Threat actors continuously scan for unpatched security flaws within software applications, hardware devices, and network infrastructure. These vulnerabilities provide entry points for injecting malicious code directly into target systems or firmware.
Internet of Things (IoT) devices present particularly attractive targets due to their frequent deployment with minimal security configurations. Many IoT manufacturers prioritize functionality over security, leaving devices vulnerable to exploitation once deployed in home or business environments.
Malvertising and drive-by downloads
Hackers exploit digital advertising networks as sophisticated vectors for distributing malware, injecting malicious code into legitimate ads via advertising platforms and content delivery networks.
Drive-by download attacks require no user interaction beyond visiting a compromised website, automatically initiating malware installation. Automatic redirects remain a significant threat to advertising technologies and users, allowing malware installation.
How to Protect Against Malware
Effective protection against malware requires a combination of user awareness and the implementation of responsive technical security measures.
Since human error remains a significant vector for infection, user vigilance and the adoption of strict rules are a key factor in protecting against malware, just as essential as the use of security tools to defend computers and networks against intrusion.
Be vigilant and adopt safe practices
The human factor remains the most critical component of malware defense, as many successful attacks exploit user behavior rather than technical vulnerabilities. Phishing and social engineering are particularly common threats using manipulative techniques to persuade individuals to perform actions that compromise their safety.

Stay alert with email security
Adopt a strict email protection policy: emails remain a primary distribution channel for malware and special attention must be paid to all incoming messages.
Emails from unknown senders may contain suspicious attachments or images that could contain malware disguised as legitimate communications. Procedures should be put in place for staff to verify attachments and unexpected emails, even those from known contacts whose accounts may have been compromised.
Adopt safe download practices
Downloads are one of the main ways malware can get into your system. Always carefully check the source and details of content before downloading or running a downloaded file.
Organizations should establish approved software repositories and prohibit the installation of unauthorized applications from unknown sources. Verifying the authenticity of software through official vendor channels helps prevent the installation of applications containing Trojan horses.
Keep your web browsing safe
Web browsing has a significant impact on the risk of infection because it exposes you to malicious websites.
For example, websites displaying pop-up windows claiming that your computer is infected and asking you to download software are a common tactic used by malware distributors.
Legitimate software publishers never distribute their products through unsolicited pop-up ads or aggressive tactics claiming that your computer is immediately at risk of infection.
Stay alert to social engineering techniques
Awareness of social engineering goes beyond simple emails and must include phone calls, text messages, and in-person interactions. Attackers may combine multiple communication channels to establish credibility and pressure their targets into compromising security protocols.
Implement Technical Safeguards
Beyond personal vigilance, additional measures and well-designed protection tools are necessary to protect against infections, as even downloads from legitimate sites can sometimes carry malware. No protection is absolute.
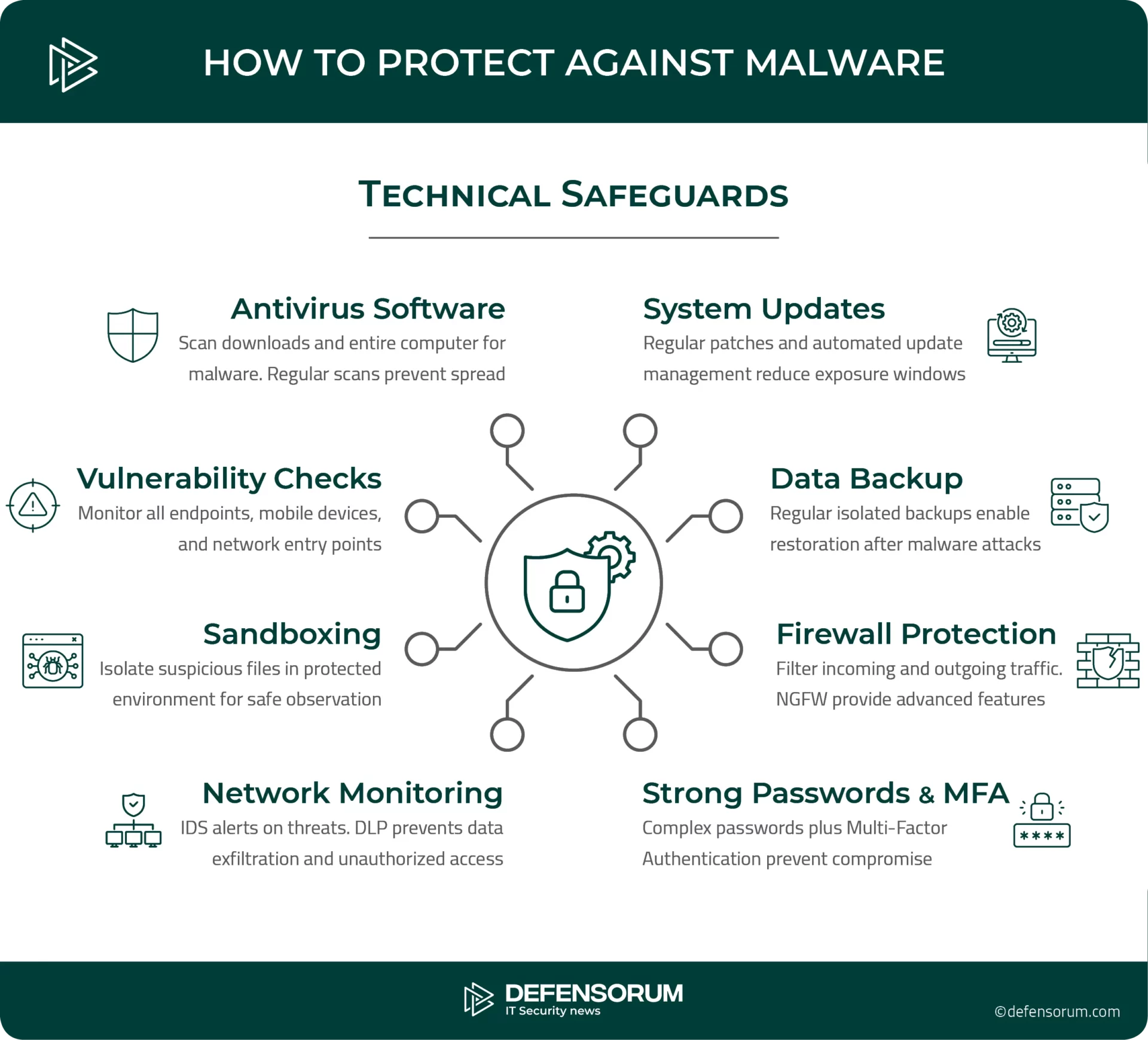
Use effective antivirus software
Antivirus programs can scan downloads for malware before opening them and scan the entire computer for existing malware. Regular scans are recommended to quickly detect malware and prevent its spread.
Back up data
Regular data backup is a preventive mitigation strategy. If a malware attack is successful, a clean backup can be used to restore an infected device after wiping it. Backups should be isolated and shielded from malware.
Check for vulnerabilities
Implement a comprehensive cybersecurity system to identify potential entry points for malware into a network. A proactive security system should monitor all endpoints (including mobile devices) and servers, both on-premises and in the cloud. Malware can infect different types of endpoints, including mobile phones, mobile devices, and IoT devices, especially those connected to corporate networks running older, vulnerable operating systems. Unsecured devices, unsecured networks (supply chain, third-party partners), file servers, file-sharing software, P2P file sharing, and remotely exploitable network vulnerabilities can all open up attack vectors.
Use strong passwords and multi-factor authentication (MFA)
Strong password policy requires complex combinations that resist brute force attacks and credential stuffing campaigns commonly used by malware actors. Multi-factor authentication adds a second layer of security by requiring additional verification beyond passwords, such as smartphone-generated codes or biometric authentication. This significantly reduces the risk of account compromise, even when passwords are exposed to phishing attacks or data breaches, because attackers cannot access protected systems without the additional authentication factors.
Regularly update the system and patch
Regular system updates are the basis of technical safety to protect against malware attacks. Operating system and application updates often include security patches that improve protection against intrusions and must be installed quickly to prevent breaches. Implementing an automated patch management system is a good way to quickly deploy security updates across an organization’s networks, thereby reducing the windows of exposure exploited by hackers.
Isolate suspicious files with sandboxing
Sandboxing is the practice of isolating a piece of software so that it can access only certain resources, programs, and files within a computer system. This blocks malware attacks by isolating suspicious software in a protected environment, allowing IT teams to observe their behavior without endangering the rest of the network.
Use firewall protection
Firewall technology helps prevent malware delivery by filtering incoming and outgoing network traffic. This dual protection is essential because malware already present in a system can affect users, devices, and connected networks. Next-generation firewalls (NGFW) now incorporate advanced features like packet filtering, network monitoring, and deeper inspection to protect against intrusions and application hijacking.
Ensure network monitoring and data protection across all resources
Intrusion detection systems (IDS) are network security tools that actively monitor suspicious traffic patterns and alert potential threats, preventing malware-related incidents from escalating into data breaches. Data loss prevention (DLP) is also a key component for monitoring, detecting, and blocking attempts to transmit sensitive data across network boundaries, email systems, and removable storage devices. The goal is to identify confidential information before any unauthorized exfiltration occurs, whether through malware, an internal threat, or accidental disclosure.
Use Zero-Trust Network Access (ZTNA), Cloud Access Security Broker (CASB), and Secure SD-WAN.
These integrated security tools help prevent cyberattacks by implementing precise authentication and authorization controls across network infrastructure. This approach enables automated access management that determines which users and devices can reach specific network segments, systems, and applications, regardless of whether resources are located on-premises or in remote environments. CASB solutions provide additional visibility and control over cloud application usage, ensuring consistent security policies across hybrid IT environments as part of a comprehensive Secure Access Service Edge (SASE) framework.
What are the Signs of a Malware Infection?
By definition, malware infections are difficult to detect, as they are designed to spread without users’ knowledge. Most often, malware is discovered after it has carried out its malicious objectives, for example when an organization is facing a ransom demand or its technical infrastructure is blocked. However, there are certain weak signals that may indicate that a system has been infected by malware and should be monitored.
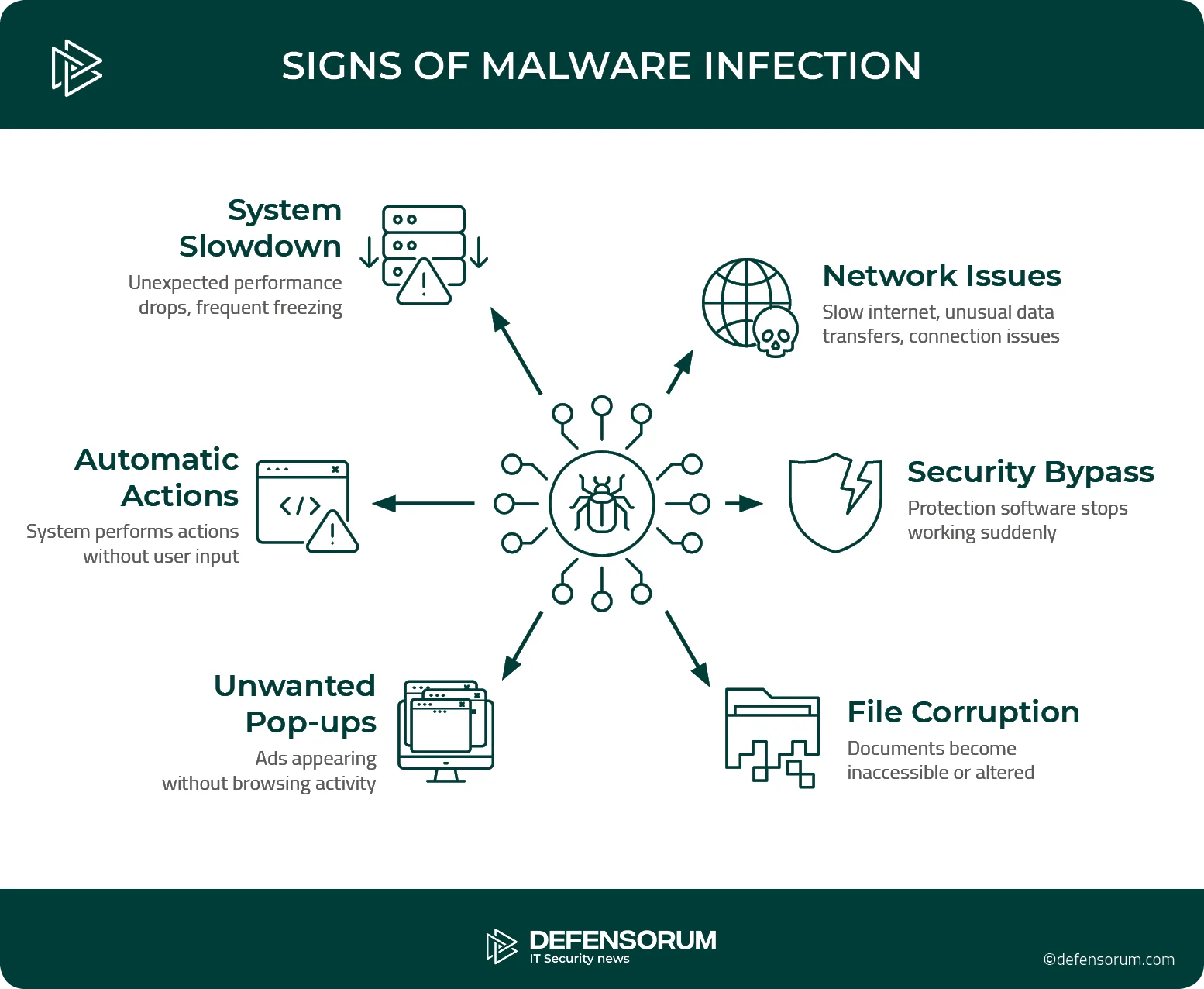
Recognizing potential malware infection symptoms early enables faster response and minimizes damage. While these indicators don’t always confirm infection, their presence warrants immediate investigation.
System Performance Issues
Unexplained performance issues often indicate malware presence. Computers running significantly slower than normal may be compromised, particularly when this slowdown occurs suddenly rather than gradually over time.
System instability manifesting through frequent crashes, freezes, or unexpected restarts can potentially result from malware consuming resources or interfering with critical operating system components.
Process monitoring tools is a good way to reveal unfamiliar programs consuming resources: excessive CPU, memory, or network utilization without corresponding user applications may suggest background malware operations.
Unusual System Behavior
Programs or execution windows that open and close on their own indicate a risk of remote control of the system, allowing hackers to access and manipulate the device without user intervention.
Security software that disables itself, particularly when users cannot restart or reinstall protection tools, is a critical sign of a malware designed to prevent removal. Advanced threats specifically target and disable security measures as a first step before executing their malicious actions.
Visual and Interface Changes
Excessive pop-up advertisements appearing is a clear sign of an adware infection. These intrusive advertisements typically contain misleading messages or additional links to other malware.
If changes you made to a browser, such as adding new toolbars, extensions, or changing the home page settings, reappear after being deleted, this clearly indicates the presence of browser-based malware. These changes can redirect searches and web traffic to malicious servers or links.
Network and Connection Anomalies
Network activity fluctuations, such as slower connection speeds or increased data usage when the computer appears idle, often result from malware communicating with command and control servers or transferring stolen data.
The same way, network monitoring tools can reveal unusual network connections to unfamiliar servers, which is the sign of a malware communicating with remote control infrastructure.
Data and File Changes
Unusual file modifications, such as changes to the name or size of existing documents, can indicate encryption or corruption by malware. Files that cannot open with their associated programs may be a sign of infection by malicious code.
Mobile Device Indicators
While mobile devices can present distinctive signs of malware infection, such as unexpected battery drain, unusual text messages sent from the device, or unexplained charges on mobile service bills, the main vector of infection is most often malicious apps. Their malicious objectives are undetectable, but they can serve as a gateway for malware to execute its actions.

How to report malware incidents and scams?
Reporting malware incidents serves several important purposes: enabling authorities to track threat trends and prosecute cybercriminals, helping the cybersecurity community understand evolving attack methods, and facilitating the development of improved defense strategies that benefit all organizations facing similar threats.
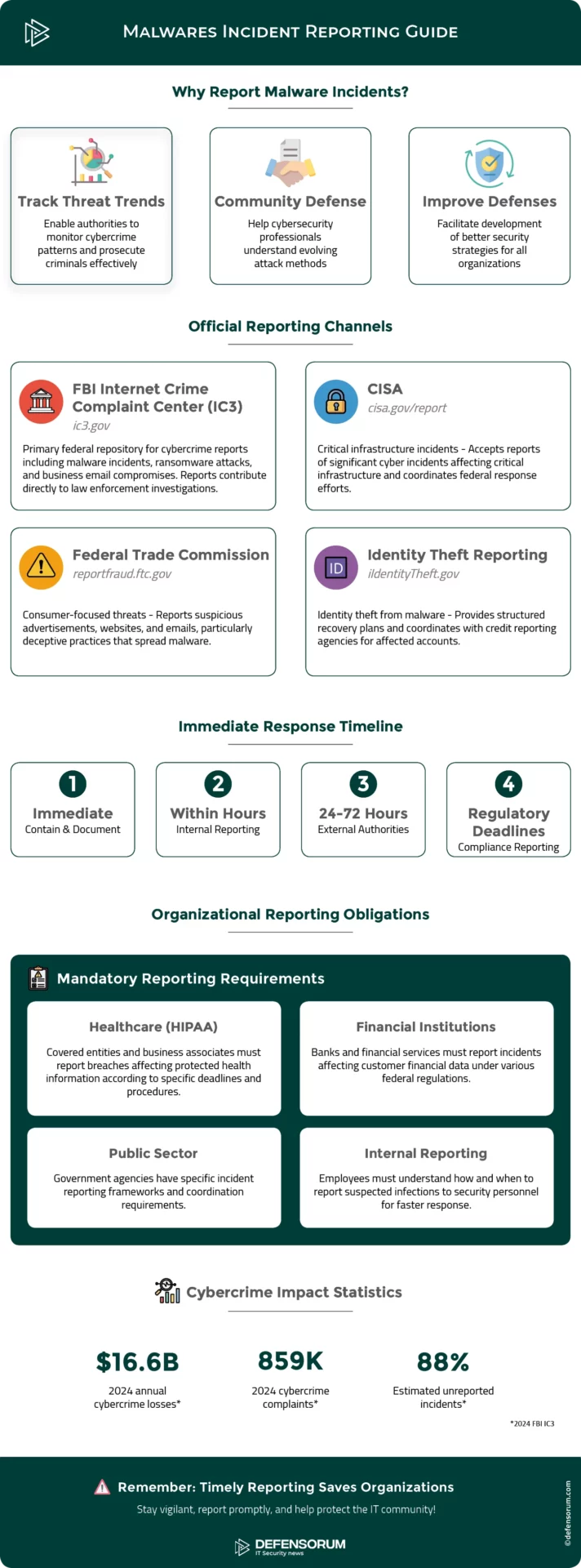
What are the official channels to report malware?
The FBI’s Internet Crime Complaint Center (IC3) serves as the primary federal repository for cybercrime reports, including malware incidents, ransomware attacks, and business email compromises. These reports contribute directly to law enforcement investigations and threat intelligence gathering.
The Cybersecurity and Infrastructure Security Agency (CISA) accepts reports of significant cyber incidents affecting critical infrastructure and coordinates between federal agencies and private sector organizations during major security events.
The Federal Trade Commission accepts reports of suspicious advertisements, websites, and emails through its fraud reporting system, focusing particularly on threats targeting consumers and deceptive practices that spread malware.
Ransomware attacks should be immediately reported to local law enforcement and federal agencies via the IC3. This information helps track criminal groups and develop appropriate countermeasures against specific ransomware variants.
Identity theft resulting from malware requires prompt action via IdentityTheft.gov. This reporting mechanism provides structured recovery plans based on specific compromise circumstances and coordinates with credit reporting agencies to flag affected accounts.
What reporting obligations apply to organizations?
Organizations that fall victim to malware infections may be subject to mandatory reporting obligations depending on the data involved. Healthcare organizations (and their business partners), financial institutions, and public sector providers are subject to specific regulatory frameworks that require formal notification of security incidents.
For example, the Health Insurance Portability and Accountability Act (HIPAA) imposes stricter reporting requirements on all covered entities (including business associates), with specific deadlines for reporting breaches affecting protected health information to authorities, depending on the severity and scope of the incident.
Internal reporting within organizations enables adequate coordination of incident response. Employees must clearly understand how and when to report suspected infections to the appropriate security personnel in order to facilitate faster containment and remediation.
Why is information sharing essential for cybersecurity
Participation in information-sharing communities strengthens collective defense capabilities. Industry-specific groups exchange threat indicators and effective countermeasures, creating a broader security intelligence network than any single organization could develop.
Detailed documentation of incidents helps security teams identify attack patterns. Preserving information about infection methods, system behaviors, and effective remediation techniques builds an organizational knowledge base for dealing with future threats.
Images credit: AdobeStock







