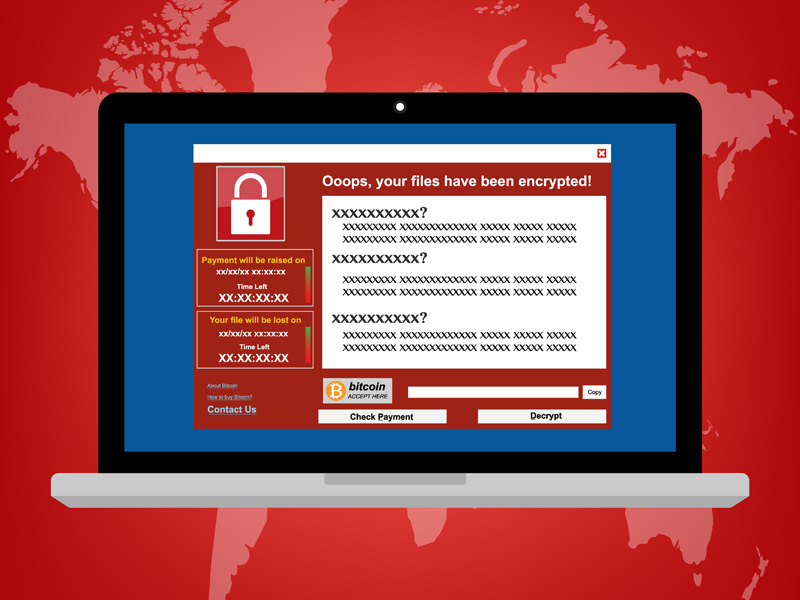
There has been a huge increase in WannaCry ransomware attacks around the globe, including a new campaign being launched on Friday the 13th of May 2017. Unlike previous WannaCry ransomware attacks, the present campaign takes advantage of a vulnerability that is found in Server Message Block 1.0 (SMBv1).
Zero day exploits are often employed by cybercriminals, however this example would appear to have been originally developed by the National Security Agency (NSA). It was then stolen and passed to the Shadow Brokers hacking gang. The exploit was published by Shadow Brokers in April 2017, with the gang responsible for this attack having combined it with a worm that is capable of spreading quickly in order to impact every vulnerable networked machine.
Microsoft released a patch on the 13th of March 2017 (MS17-010) which acted to block ETERNALBLUE exploit attacks. Nonetheless, the large number of WannaCry ransomware attacks already reported would suggest that numerous organizations have not yet applied the patch.
Organizations affected include Deutsche Bahn of Germany, Telefonica of Spain, FedEx and the National Health Service of the UK. Numerous of NHS Trusts throughough the United Kingdom fell victim to the WannaCry ransomware attacks on Friday the 12th of May. Although confident that patient data was not obtained by the attackers, the NHS was obliged to shut down its systems and cancel operations while mitigating work against the attack was being carried out.
On the morning of the 13th May, WannaCry ransomware attacks were reported by organizations in approximately one hundred countries. Although unclear at this point how many computers were in fact encrypted by the ransomware, the antivirus firm Avast alone has already identified some 57,000. The final figure will no doubt be significantly higher.
As soon as it has been installed, the WannaCry ransomware searches for other vulnerable machines and quickly proceeds to infect all vulnerable devices. The ransom demanded may be as little as $300, however that figure will of course be multiplied by the number of devices that have been successfully infected. Moreover, the demand doubles after just three days, with decryption keys being destroyed by the attackers after one week if the ransom has not been paid. Following that, recovery will be impossible without a viable backup. At present here is no decryptor available for WannaCry ransomware.
Organizations need to patch Windows and plug the vulnerability in order to protect themselves from attack.
These attacks should be taken as a stark warning to all organizations that they need to apply patches as soon as possible, especially those patches which rectify critical vulnerabilities for which exploits have been created and made public online.