Emma Taylor
Cybercriminals with Nation-State Support Responsible for Yahoo Attack
InfoArmor has claimed that data from the Yahoo breach of over one billion user accounts has already been purchased on the black market by multiple third parties on numerous occasions. Although Yahoo argues that a nation-state sponsored group was responsible … Read more
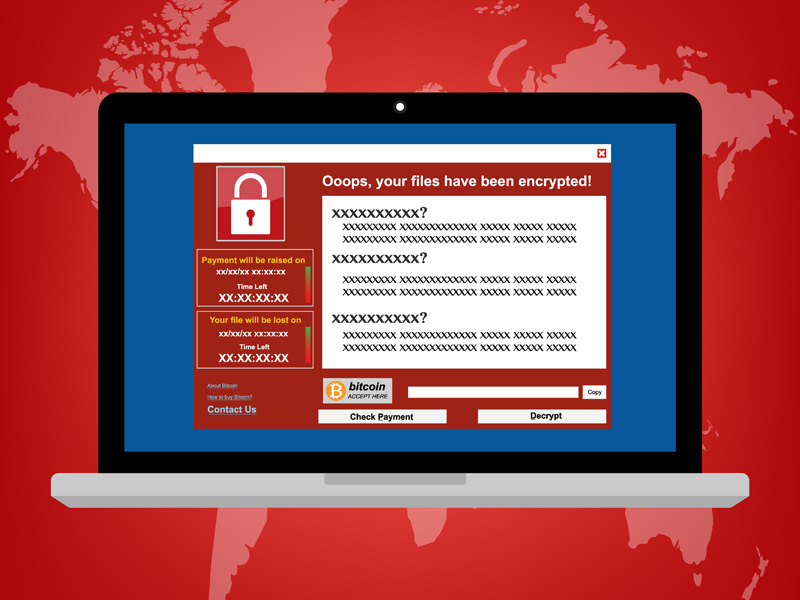
Global Reports of WannaCry Ransomware Attacks
There has been a huge increase in WannaCry ransomware attacks around the globe, including a new campaign being launched on Friday the 13th of May 2017. Unlike previous WannaCry ransomware attacks, the present campaign takes advantage of a vulnerability that … Read more
US-Certs: SSL Inspection Tools Might Make Cybersecurity Weaker
A recent warning issued by US-CERT has advised that SSL inspection tools may actually do the opposite of what they are intended for; i.e. they might serve to weaken the cyber defenses of healthcare organizations’ rather than strengthen them – … Read more
Rapid Account Verification Being Offered by New Twitter Credit Card Phishing Scam
Proofpoint, the cybersecurity firm, has confirmed that is has discovered a new Twitter credit card phishing scam. Users of the social media platform Twitter are being offered verified account status via native Twitter ads; the catch being that signing up … Read more
Windows Dialog Box Mimicked By Newly Discovered Trojan Downloader
Dr. Web, a Russian antivirus firm has recently discovered a new Trojan downloader. The malware uses a popup Windows ‘Save As’ dialog box to install malicious payloads, which have thus far all been adware. The malware, dubbed “Trojan.Ticno.1537”, installs variety … Read more
Wi-Fi Routers Infected by Switcher Trojan through Android Mobiles
Kaspersky Lab has identified a highly dangerous new Trojan which has been used to attack Wi-Fi routers through Android devices. The new form of malware, which has been dubbed the Switcher Trojan, is presently being employed to attack routers based … Read more
Erie County Medical Center Patients Put at Risk by Apparent Ransomware Attack
Ashland Women’s Health confirmed in April 2017 that it had been the victim of a significant ransomware attack.19,272 Ashland patients were affected. This followed confirmation the previous week that ABCD pediatrics ransomware attack had put 55,447 patients at risk. On … Read more
SMB File Sharing Protocol Flaw Made Public Before Release of Patch
Details of a SMB file sharing protocol flaw in Windows have been made public some 12 days prior to the release of a patch by Microsoft. Laurent Gaffié, the researcher who published details of the flaw, has claimed that Microsoft … Read more
San Francisco Transport System Ransomware Attack Reported
A ransomware attack on the San Francisco Transport System in November 2016 resulted in the encryption of computers used by the city’s light rail system. The criminals responsible for the attack demanded ransom of 100 Bitcoin (approxiately $70,000) for the … Read more
Investigation into Ransomware Infection Affecting 19,000 People
One of Highmark Blue Cross Blue Shield’s (Delaware) subcontractors has fallen victim to a ransomware infection and cyberattack that may have put private information relating to almost ninetenn thousand beneficiaries of employer-paid health plans at risk. The attack happened on … Read more
Diagnostics Website Flaw at ‘True Health’ Reveals Private Patient Information
Patients of the True Health Group have had their health reports exposed online due to a law in the True Health Diagnostics website. Moreover, the reports appear to have been viewable by other patients for months if not years. Based … Read more
Sentara Healthcare: Investigation into Data Breach
Sentara Healthcare is currently carrying out an investigation into a data breach affecting one of its 3rd-party vendors which allowed a number of patients’ protected health information to be accessed by an unauthorized person. Sentara Healthcare was alerted to a … Read more
Yahoo Breach Investigated By U.S. Securities and Exchange Commission
It has been confirmed that the U.S. Securities and Exchange Commission (SEC) are to investigate Yahoo concerning two enormous data breaches that were made public in late 2016. The controls put in place by Yahoo to prevent data breaches will … Read more
Samba possibly vulnerable to ‘WannaCry’-type attacks
It has been revealed that Samba might possibly be vulnerable to network worm attacks similar to those which were utilized to deliver WannaCry ransomware on the 12th of May 2017. Unix, Linux and numerous NAS devices use Samba to add … Read more
Industrial Sector targetted by Ransomware Attackers using KillDisk Variant
In late 2016, a new ransomware variant emerged which is now being used in attacks on industrial companies. Unlike other ransomware variants, the new malware does not permanently lock users’ files. Victims have been threatened with full disk deletion should … Read more
ABCD Pediatrics Hit By Ransomware Attack Affecting 55,000 Patients
The private health information relating to more than 55,000 patients may have been compromised in during a ransomware attack against ABCD Pediatrics on the 6th of February 2017. Attackers managed to access ABCD Pediatrics’ servers following which Dharma ransomware was … Read more
New Powershell Remote Access Trojan Identified
Researchers at Cisco Talos have recently identified a new Powershell Remote Access Trojan (RAT). The memory-resident malware is almost impossible to detect because it doesn’t write files to the computer’s hard drive and uses a new way of communicating with … Read more
Victims Offered A Criminal Choice by “Popcorn Time” Ransomware
New methods of spreading ransomware are constantly being developed; however, a new ransomware variant discovered by MalwareHunterTeam researchers called “Popcorn Time” appears to use tactics that have never before been seen. When Popcorn Time ransomware has infected a victims device … Read more
Ransomware Attacks Targetting Businesses Now Using PetrWrap
A new group of criminals have taken control of Petya ransomware and are using it in ransomware attacks against businesses without the participation or knowledge of those who created the ransomware. Those responsible for the new PetrWrap campaign developed Petya … Read more
Molina Healthcare Patients’ Data Exposed by Portal Security Flaw
A security flaw in a patient portal has exposed information concerning patient claims. Claims information had previously been uploaded to the patient portal of Molina Healthcare, which is a managed care company based in Long Beach, California. This in itself … Read more
“Patch Tuesday”: Sixty-eight Microsoft Vulnerabilities Repaired
Patch Tuesday 2016: Microsoft has acted to fix 68 vulnerabilities including 6 that had been rated critical. The updates have been spread over fourteen security bulletins. The updates include fixes for 2 vulnerabilities that are presently being actively exploited including … Read more
Warning Issued by OCR to Providers of Healthcare Regarding Use of HTTPS Inspection Tools
Numerous healthcare organization employ HTTPS inspection tools in order to monitor HTTPS connections for any malware which may be present. HTTPS inspection tools are used to decrypt secure HTTPS network traffic and verify content prior to re-encrypting traffic. The purpose … Read more
Thousands of Sites at Risk from Newly Identified Zero Day WordPress Vulnerability
A Sucuri researcher has recently discovered a new zero day WordPress vulnerability in the WordPress REST API. The vulnerability permits content injection and the escalation of user privileges. Should it be exploited, an unauthenticated user might be able to make … Read more
Victims Being Blackmailed by Newly Discovered Ransomware Variant
Proofpoint researchers have recently identified a previously unknown ransomware variant, known as “Ransoc”, which employs various techniques to extort money from its victims. As opposed to the encryption of a broad range of file types and then demanding that a … Read more
Recent Discovery of Social Engineering Scam on LinkedIn
A new LinkedIn social engineering scam has been uncovered by researchers at Heimdal Security which tries to convince LinkedIn users to give their personal information. The attackers have been attempting to obtain access to users’ financial data together with identity … Read more
Latest Business Email Compromise Scam Methods Revealed
Numerous email compromise tactics have for some time been in use by scammers to trick business executives into making fraudulent wire transfers. Recently, a Symantec security specialist has observed that some scammers have begun taking a new approach in order … Read more
Vulnerability in Netgear Router leads to US-CERT Alert to Replace Devices
A Netgear router vulnerability which remained unpatched for approximately 3 months was recently made public, a disclosure which placers users at risk of their devices being exploited by hackers. The threat is so large that US-CERT issued a strong warning … Read more
Microsoft Security Bulletins to be discontinued In January 2017
If yours is one of many businesses which depend upon Microsoft Security Bulletins to remain informed about new patches and fixes to known vulnerabilities, you and your colleagues should prepare yourselves for an upcoming change in the way Microsoft announces … Read more
Data Breach at Med Center Health affects almost 160,000 of its Patients
The FBI has been investigating a large Med Center Health data breach that affects many affiliates and approximately 160,000 patients. Hackers are not believed to be responsible for the Med Center Health data breach, in fact it is thought that … Read more
Madison County Invests $220K in Cybersecurity Following Ransomware Attack
The payment of a $21,000 ransom to attackers following the Madison County ransomware attack that disabled a large number of the county’s computer systems in November 2016 was necessitated as a viable backup of the data concerned did not exist. In accordance … Read more
Malicious Word Macros Responsible for Spreading MacOS Malware
According to IT Security researchers, MacOS malware is now being spread by malicious Word macros. This is the first occasion on which MacOS malware has been recognised as having been used to spread this attack vector. Windows users can anticipate … Read more
$28,000 Paid for Key following January Los Angeles Valley College Ransomware Attack
A ransomware attack on an LA Valley College on the 6th of January, 2017 lead to student data being locked and resulted in some 1,800 college staff – both administrators and teachers – being unable to gain access to their … Read more
OPM Data Breach Victims targetted by Locky Ransomware Campaign
The culprits responsible for Locky ransomware have begun using data obtained in the OPM data breaches of 2014 and 2015 in a new campaign designed to spread cryptoransomware. It remains unknown exactly how much data was obtained, however in total, … Read more
2017’s Biggest Healthcare W-2 Phishing Scam Impacted 17,000 Employees
The biggest healthcare W-2 phishing scam 2017 thus far has been reported by American Senior Communities of Indiana. Although a number of organizations have already reported being tricked by phishing emails this tax season, this was by a long way … Read more
Rise in Joomla Website Attacks due to Hackers Reverse Engineering Patches
A pair of recently recognised critical vulnerabilities to the Joomla content management system are presently being utilised by hackers in a series of attacks on Joomla websites. Although the two vulnerabilities were not thought to have been exploited when first … Read more
February Sees Dramatic Rise in Insider Healthcare Data Breaches
In its most recent healthcare data breach report. Protenus has indicated that the month of February witness a significant increase in insider healthcare data breaches. The February Breach Barometer report shows that there were 31 reported healthcare data breaches during … Read more
Christmas Period Malware Infections Increase by more than 100% in 2016
Malware infections over the Christmas holiday period are something to be expected. Every year as the number of online shoppers increases, the number of Windows malware infections increases with them. Data from Enigma Software Group (ESG) indicates that between Black … Read more
Google Acts Against Repeat Malware Offending Sites
Google has promised that it will take action against websites that are used repeatedly to serve malware, unwanted software, or are used to ‘phishing’ attacks. As soon as a website has been confirmed as a repeat offender, the Google Chrome … Read more
Malicious Ransomware App Removed from Play Store by Google
An app that was available to members of the public for download from the Google Play store has been discovered to have contained ransomware. In recent days, Google acted to remove the ransomware app from its Play Store, however it … Read more
FBI Informs Healthcare Providers of Risks Associated with Anonymous FTP Server Use
According to a recent warning issued by the FBI, Healthcare organizations may be placing the protected health information of their patients in jeopardy by using anonymous FTP servers. Cybercriminals are profiting from the lack of protection on FTP servers to … Read more
Leak of 1.5 Million Player Profiles confirmed following ESEA Hacking Incident
E-Sports Entertainment Association (ESEA) has confirmed that it has been subject to an attempted extortion after a hacker successfully infiltrated one of its game servers. The incident enabled the hacker to steal the player profiles and other data of 1.5 … Read more
Disk-Wiping Malware Being Utilised to Format Virtual Desktops
Although disk-wiping malware has existed for several years, a new version of an older malware variant has now been detected. This malware is reportedly being used to attack companies which have implemented a virtual desktop infrastructure (VDI). As opposed to … Read more
85 Million Dailymotion Users effected by Cyberattack
LeakedSource has claimed that email addresses, usernames, and passwords have been accessed by the hackers responsible for a recent Dailymotion cyberattack. Dailymotion is one of the biggest internet video sharing platforms and, according to Alexa, is the world wide web’s … Read more
Cybercriminals Telephoning Customer Service Representatives to ask them to Open Malware Infected Attachments
The risk of malware and ransomware infections can be reduced by training staff to avoid opening file attachments received from unfamiliar email accounts. Despite this being common practice, a well known cybercriminal group has recently been increasing the number of … Read more
Children’s Hospital in Kansas City Alerts 5,500 Patients following Potential PHI Breach
It has been confirmed that Kansas City Children’s Mercy Hospital has now began the process of notifying more than 5,500 patients that portions of their electronic protected health information have been exposed online. It was discovered that personally identifiable information … Read more
Enterprise Firewalls Being Taken Down by Attackers Using ICMP Ping Floods
Researchers from the Danish telecom firm TDC have claimed that attackers have been using ICMP ping floods to carry out Denial of Service (DoS) attacks capable of removing enterprise firewalls. As opposed to standard DDoS attacks, the attacker does not … Read more
Confirmation of Ransomware Attack Women’s Health Centre in Kentucky
A sole-practitioner gynaecologist’s clinic in Ashland, Kentucky has become the most recent healthcare provider to be targeted by ransomware attackers. The Department of Health and Human Services’ was recently informed of the attack by Ashland Women’s Health. The healthcare practice … Read more
County Sherriff’s Office Confirms Payment of Bitcoin Ransom to Unlock Files
Cybercriminals responsible for a ransomware attack against a Sherriff’s office in Arkansas have received payment of 3 Bitcoin ($2,400) to supply the relevant keys to decrypt files that had been locked by the ransomware. Carrol County Sheriff’s office was the … Read more
Exploitation of Vulnerability in Apache Struts Revealed
Cisco Talos and Apache have issued warnings to their users following the revelation of a new Apache Struts vulnerability that has been actively exploited in recent days. Cisco Talos researchers recently identified the ‘zero-day’ vulnerability in the Java application framework … Read more
More than 1 Billion Yahoo Accounts Compromised in by 2013 Cyberattack
Yahoo confirmed in September 2016 that it had been the victim of hacking which had compromised approximately half a billion accounts; however, it has now revealed that a Yahoo cyberattack in 2013 was two times as big. Apparently, the details … Read more